
Seamless Software Integration
Easily take card payments, process transactions, and manage all your payment activity from the interface of the business management software you know and trust.
PCI Compliance & Protection Program
Get hands-on help throughout your yearly PCI renewal and quarterly security scans. Also included in the program:
• Online self-assessment questionnaire (SAQ)
• Online vulnerability scanning
• Security policy template
• Email action reminders
• PAN detection scan
• Device security scan
• Network perimeter scan
• PCI toolkit
• Up to $20,000 in Breach Financial Assistance

Competitive Processing Rates
As a premier payment services provider, we’re able to command very competitive rates — to keep processing from eating up your bottom line.
In fact, the combination of an integrated payment system and our competitive rates often yields substantial net savings for businesses depending upon their business type and processing volume.
Interactive Customer Portal
Within your payments portal, you have access to statements from the past 13 months, as well as the ability to:
- Filter by business location, statement type, or date
- Get greater details on deposits, fees, batches, and transactions by clicking on any value
- Download real-time reports in PDF or CSV format

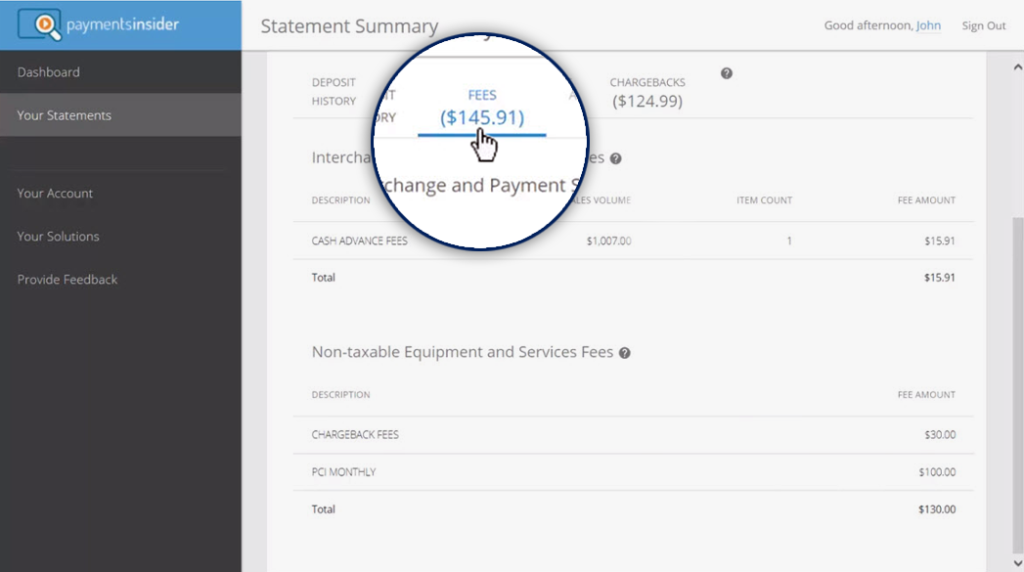
Easy-to-Read Statements
Charts and graphs give you a quick visual read of your monthly fees and volume trend. Helpful tables break down transactions by sales, returns, chargebacks, card, dollar amounts, transaction amounts and average ticket price.
What Our Clients Say
Todd Spears
“Constellation’s service is impeccable; their team is responsive, and they actually care that you’re a customer. I’ve already directed over 5 new businesses to their service.”
Contact Us
Merchant Support
Call toll-free 888.244.2160
(Monday through Friday: 9 am – 7 pm ET)
Submit a support ticket
New Merchants
Call toll-free 888.244.2160
(Monday through Friday: 8 am – 5 pm ET)
sales@csipay.com
Take the Next Step
Make payments a simple part of your business. Fill out the form below for more info, and we’ll be in touch with you shortly.
